Forums » Discussions » 100-101試験対策、100-101テスト内容
我々の目標は100-101試験を準備するあなたにヘルプを提供してあなたに試験に合格させることです。この目標を達成するために、我々Pass4Testは時間とともに迅速に発展しています。今まで精確的な問題集を開発しています。我々の100-101問題集を利用しているあなたは一発で試験に合格できると信じています。心配なく我々の資料を利用してください。
Facebook 100-101 認定試験の出題範囲:
| トピック | 出題範囲 |
|---|---|
| トピック 1 |
|
| トピック 2 |
|
| トピック 3 |
|
| トピック 4 |
|
| トピック 5 |
|
| トピック 6 |
|
| トピック 7 |
|
| トピック 8 |
|
100-101テスト内容、100-101トレーニング費用
100-101実践教材は、すべての点で同様の製品よりも優れていると自信を持って伝えることができます。まず、ユーザーは100-101試験準備を無料で試用して、100-101スタディガイドをよりよく理解することができます。ユーザーが製品が自分に適していないことに気付いた場合、ユーザーは別の種類の学習教材を選択できます。ユーザーの選択を尊重し、ユーザーが100-101実践教材を購入する必要があることを強制しません。ユーザーが適格な100-101試験に合格できるように、ユーザーのすべての要件を可能な限り満たすことができます。
Facebook Meta Certified Digital Marketing Associate 認定 100-101 試験問題 (Q30-Q35):
質問 # 30
What are two common TCP applications? (Choose two.)
- A. SMTP
- B. SNMP
- C. FTP
- D. DNS
- E. TFTP
正解:A、C
解説:
SMTP uses TCP port 25, while FTP uses TCP ports 20 and 21. http://pentestlab.wordpress.com/2012/03/05/common-tcpip-ports/
質問 # 31 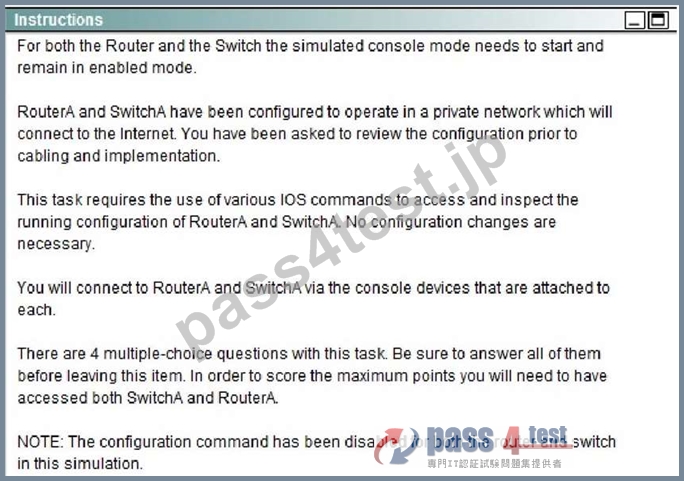

Select two options which are security Issues which need to be modified before RouterA is used? (Choose two.)
- A. unencrypted weak password is configured to protect privilege mode
- B. configuration supports un-secure web server access
- C. virtual terminal lines have a password, but it will not be used
- D. inappropriate wording in banner message
- E. the virtual terminal lines have a weak password configured
正解:C、D
解説:
Explanation/Reference:
This answer can be done by simulation only, don't know user name password and banner message etc
質問 # 32
Which layer of the OSI model controls the reliability of communications between network devices using flow control, sequencing and acknowledgments?
- A. Physical
- B. Network
- C. Transport
- D. Data-link
正解:C
解説:
There are many services that can be optionally provided by a transport-layer protocol, and different protocols may or may not implement them. Connection-oriented communication: It is normally easier for an application to interpret a connection as a data stream rather than having to deal with the underlying connection-less models, such as the datagram model of the User Datagram Protocol (UDP) and of the Internet Protocol (IP). Byte orientation: Rather than processing the messages in the underlying communication system format, it is often easier for an application to process the data stream as a sequence of bytes. This simplification helps applications work with various underlying message formats. Same order delivery: The network layer doesn't generally guarantee that packets of data will arrive in the same order that they were sent, but often this is a desirable feature. This is usually done through the use of segment numbering, with the receiver passing them to the application in order. This can cause head-of-line blocking. Reliability: Packets may be lost during transport due to network congestion and errors. By means of an error detection code, such as a checksum, the transport protocol may check that the data is not corrupted, and verify correct receipt by sending an ACK or NACK message to the sender. Automatic repeat request schemes may be used to retransmit lost or corrupted data. Flow control: The rate of data transmission between two nodes must sometimes be managed to prevent a fast sender from transmitting more data than can be supported by the receiving data buffer, causing a buffer overrun. This can also be used to improve efficiency by reducing buffer underrun. Congestion avoidance: Congestion control can control traffic entry into a telecommunications network, so as to avoid congestive collapse by attempting to avoid oversubscription of any of the processing or link capabilities of the intermediate nodes and networks and taking resource reducing steps, such as reducing the rate of sending packets. For example, automatic repeat requests may keep the network in a congested state; this situation can be avoided by adding congestion avoidance to the flow control, including slow-start. This keeps the bandwidth consumption at a low level in the beginning of the transmission, or after packet retransmission. Multiplexing: Ports can provide multiple endpoints on a single node. For example, the name on a postal address is a kind of multiplexing, and distinguishes between different recipients of the same location. Computer applications will each listen for information on their own ports, which enables the use of more than one network service at the same time. It is part of the transport layer in the TCP/IP model, but of the session layer in the OSI model.
質問 # 33
Refer to the exhibit.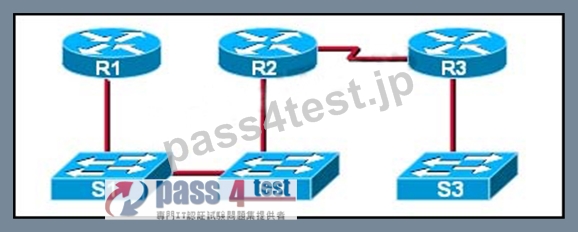
If CDP is enabled on all devices and interfaces, which devices will appear in the output of a show cdp neighbors command issued from R2?
- A. R1, S1, S2, and R3
- B. R1 and R3
- C. R2 and R3
- D. R1, S1, S2, R3, and S3
- E. R3 and S2
正解:E
解説:
A Cisco device enabled with CDP sends out periodic interface updates to a multicast address in order to make itself known to neighbors. Since it is a layer two protocol, these packets are not routed. So the devices detected would be immediate connected neighbors.
質問 # 34
A company has placed a networked PC in a lobby so guests can have access to the corporate directory.
A security concern is that someone will disconnect the directory PC and re-connect their laptop computer and have access to the corporate network. For the port servicing the lobby, which three configuration steps should be performed on the switch to prevent this? (Choose three.)
- A. Configure the switch to discover new MAC addresses after a set time of inactivity.
- B. Statically assign the MAC address to the address table.
- C. Set the port security aging time to 0.
- D. Create the port as an access port.
- E. Create the port as a trunk port.
- F. Enable port security.
- G. Create the port as a protected port.
正解:B、D、F
解説:
Explanation/Reference: If port security is enabled and the port is only designated as access port, and finally static MAC address is assigned, it ensures that even if a physical connection is done by taking out the directory PC and inserting personal laptop or device, the connection cannot be made to the corporate network, hence ensuring safety.
質問 # 35
......
Pass4Testの100-101無料デモの合格率に関する記録で実証されているように、Facebook合格率は設立当初から98%〜99%の歴史的記録を維持しています。 現時点では、100-101テストトレントの合格率は他の試験テストの合格率と比較して最高と言えますが、着実に進歩しているという真実を知っているため、専門家全員が現在の結果に満足することはありません 100-101準備資料は、Meta Certified Digital Marketing Associateの100-101試験問題作成の分野で永久に勝つことができますか。
100-101テスト内容: https://www.pass4test.jp/100-101.html